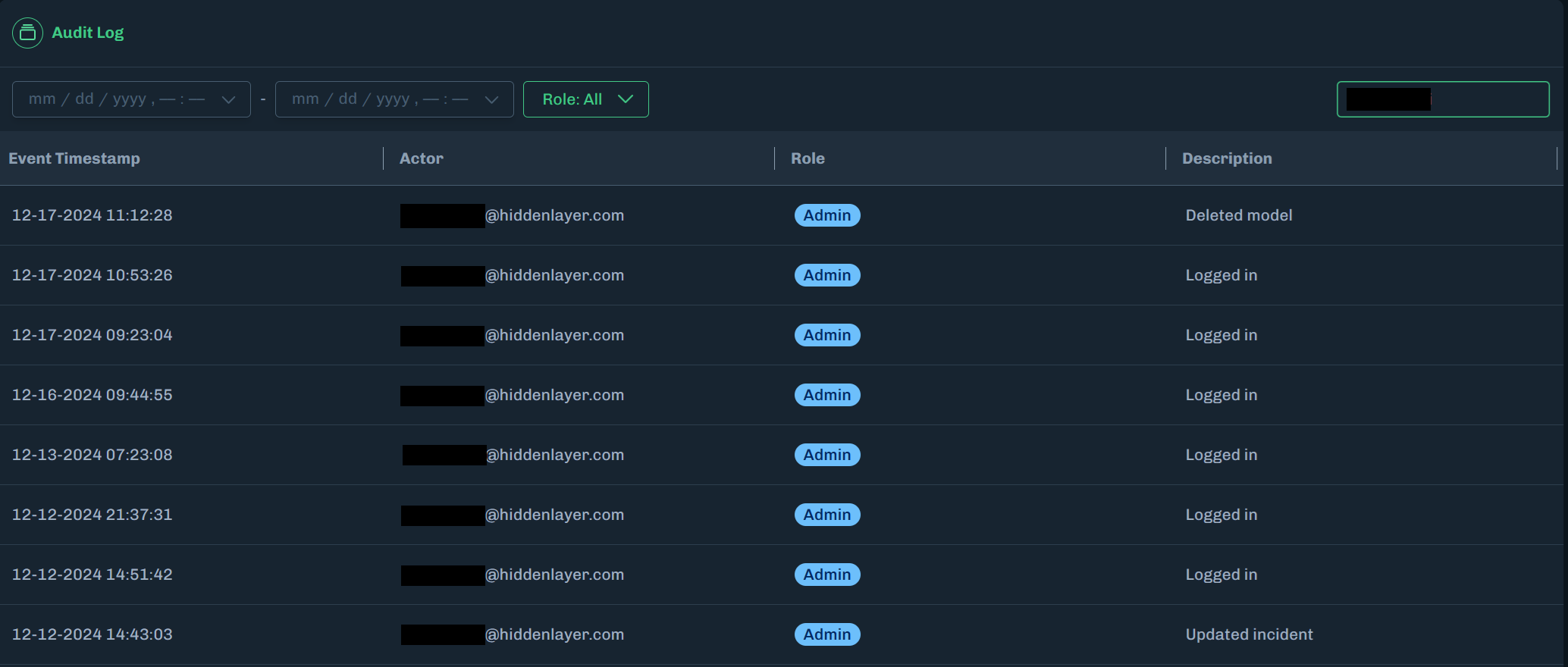
Administrators can view the Console audit log to see user activity in the Console.
Information gathered includes: the event timestamp, the user’s email address, the user’s assigned role, and a description of the activity (examples: Logged in, Created model, Updated user).
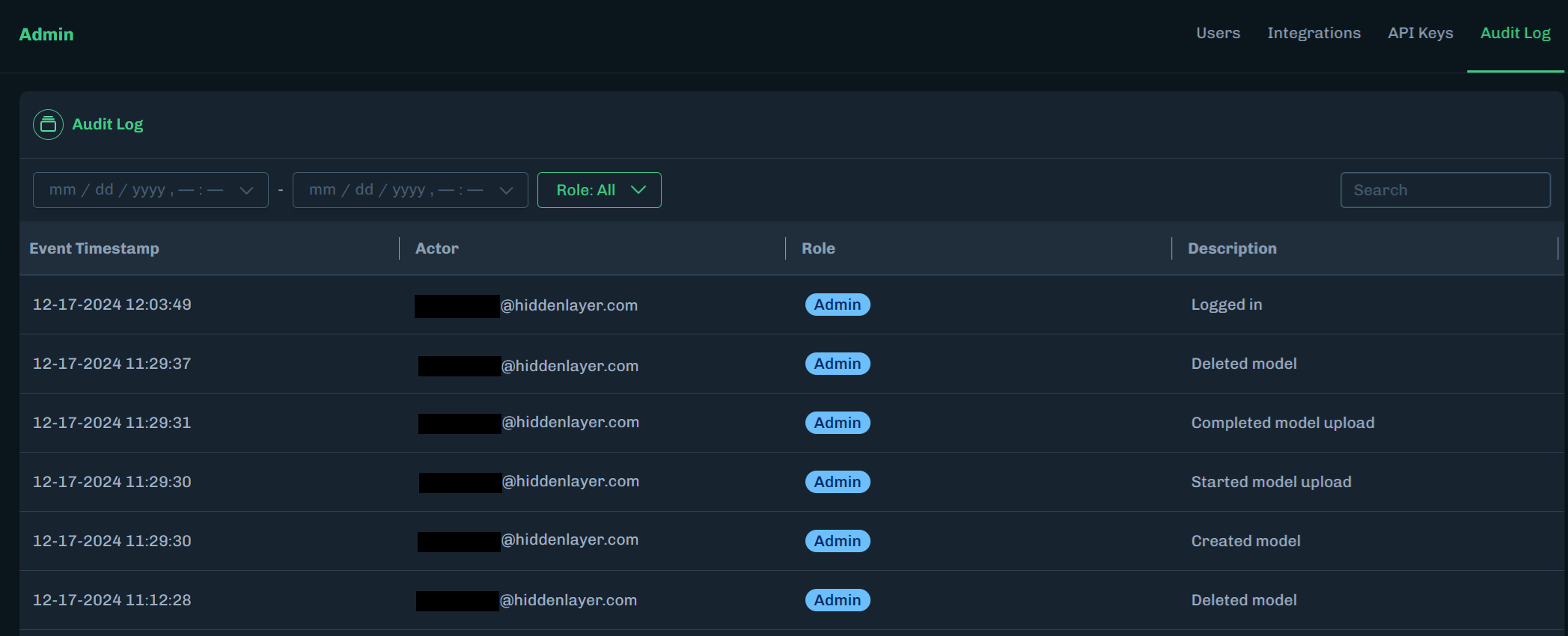
Select a start date and end date to display audit log activity that occurred within the selected dates.
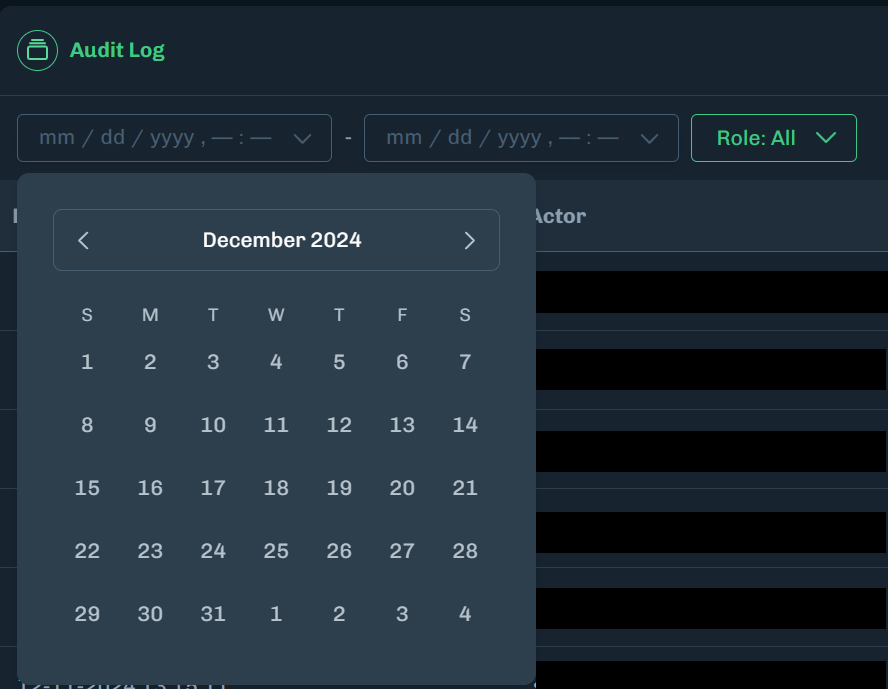
Select a role to display audit log activity based on a user’s assigned role.
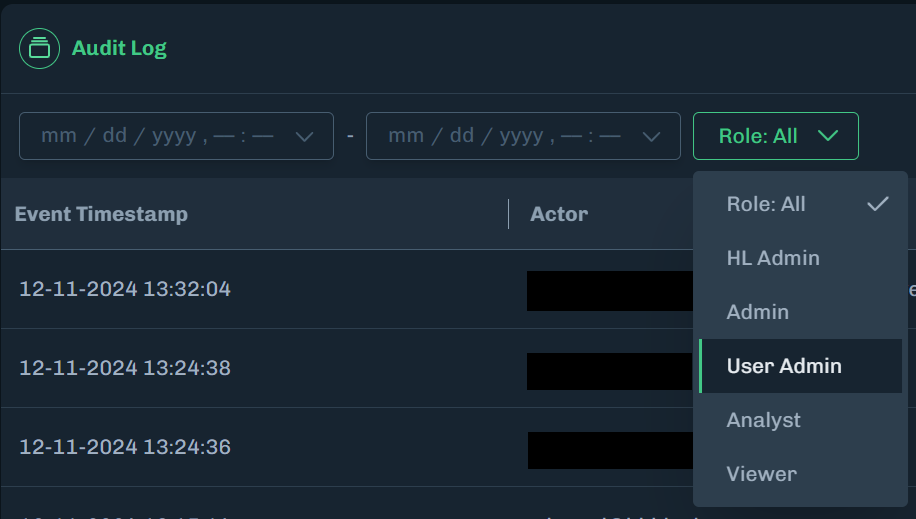
Use the search field to display audit log activity based on the user’s email address.
You must enter the full username in the email address. If the user’s email address is [email protected], then use username to search by the email address.
Audit log entries are retained for 365 days.
The following are audit log description categories and the associated log entries.
| Category | Log Entry |
|---|---|
| API Key Management |
|
| Azure ML Integration |
|
| Databricks Integration |
|
| EULA |
|
| Incident |
|
| Model |
|
| Sentinel Integration |
|
| Splunk Integration |
|
| SSO Integration |
|
| User |
|
| Webhook Integration |
|