The Supply Chain Policy establishes the criteria for evaluating scan results. By default, this policy is applied to all scanned models.
The Supply Chain Policy determines if the results of a model scan are Compliant or Noncompliant. This data appears in the Asset Scans table on the Model Scanner page and on the Detection Summary page.
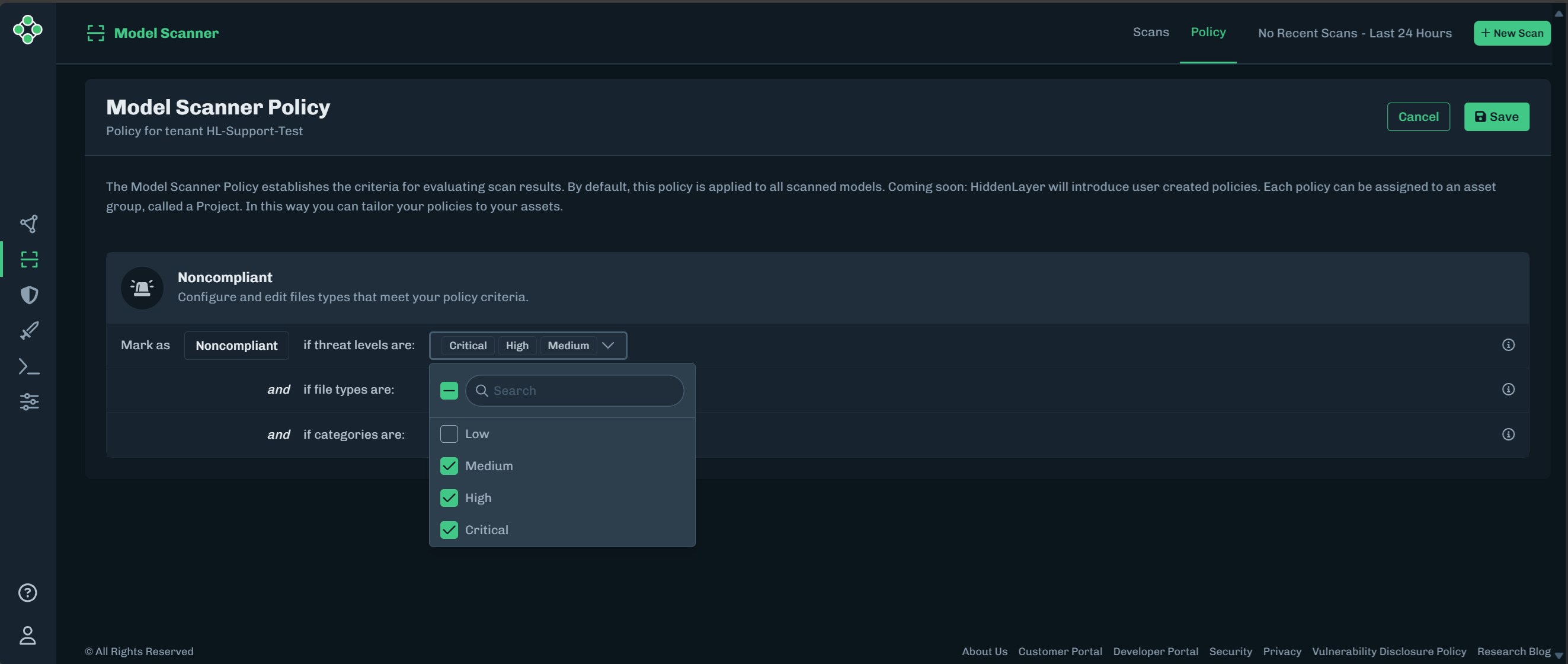
A model scan policy focuses on the items selected and ignores the unselected items.
For example: If a pickle file is scanned that results in a Suspicious Functions category with a Medium threat level.
- If pickle, Suspicious Functions, and Medium are all selected in the policy, the scan result is labeled as Noncompliant.
- If any item (pickle, Suspicious Functions, or Medium) are not selected in the policy, the scan result is labeled as Compliant.
- If the scan results in Unscanned models or Failed Scan, the scan is marked as Noncompliant.
- If the scan is labeled as Unknown, most likely the scan occurred before the policy feature was enabled.
Configure and edit files types that meet your policy criteria. There is one Supply Chain policy that is applied to all model scans.
In the console, click Supply Chain in the side navigation.
Click the Policy in the side navigation.
Click Edit.
For each policy list (threat levels, file types, and categories), select the items to include in the policy. Unselected items are ignored by the Noncompliant policy.
- Example: If the Low threat level is deselected in the policy, then any scans that only have Low threat levels are marked as Compliant.
Click Save.
Unscanned models and Failed Scans are marked as Noncompliant by default.
Updating the model scan policy is an event recorded in the audit log. In the console, click the View Audit Log link to go to the audit log page. See the Audit Log documentation for more information.
| Category | Description | Available options |
|---|---|---|
Threat levels | The threat level based on the scan results.
| Critical, High, Medium, Low |
File types | The file types included in the policy.
| NEMO, numpy, onnx, pickle, pytorch, RDS, safetensors, skops, tensorflow, unknown, ZIP, CONFIGURATION, GIT_CONFIGURATION, INITIALIZATION, JAVASCRIPT, MARKDOWN, PLAINTEXT, PNG, PYTHON, SHELL_SCRIPT, YAML, and TAR |
Categories | Detection categories included in the policy.
| Denial / Disruption of Service, Remote Code Execution, Improper Authentication, Unsecured Credential Storage, Arbitrary Code Execution, Arbitrary Read Access, Arbitrary Write Access, Arbitrary Read-Write Access, Out of Bounds Memory Read Access, Out of Bounds Memory Write Access, Network Requests, Suspicious Functions, Directory Traversal, Denial of Service, Decompression Vulnerabilities, Data Leakage Through Serialized Objects, Embedded Payloads, Fault Injection, Prompt Jailbreaking, Prompt Hijacking, Prompt Leaking, Indirect Prompt Injection, Code Injection, Excessive Agency / Permission Manipulation, Sensitive Data Leakage, Data Poisoning in Static ML, Data Poisoning in Online Learning, Data Poisoning in Federated Learning, Label Manipulation, Model Poisoning, Neural Payload, Graph Payload, Model Evasion, Training Data Extraction / PII Leakage, Model Extraction / IP Leakage, Membership Inference Attacks, Denial / Disruption of Service via Input Manipulation, Suspicious File Format, Repository Sideloading, and Control Vector |